2.7 KiB
+++ title = "How we hacked the school voice announcement system" date = 2022-04-19 draft = false
[taxonomies] categories = ["Hardware"]
[extra] author = "Emil Miler" +++
Me and some of my students have been spending free time in one of our classrooms, as we usually do, and we started thinking about hacking the ancient school voice announcement system -- injecting a custom signal and playing our own audio throughout the whole building.
System analysis
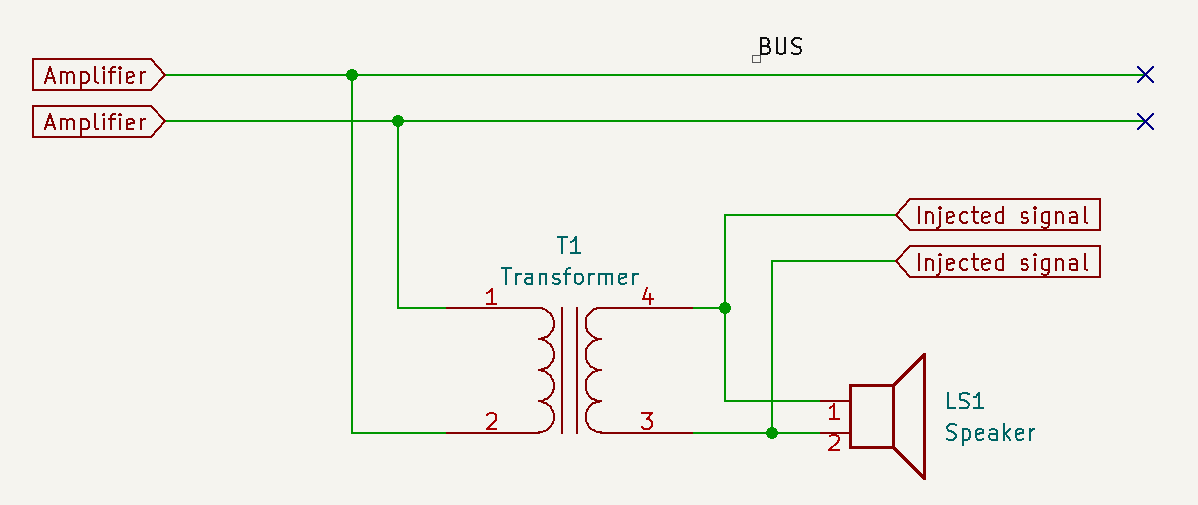
Our first thought was to analyze how the system works. It is an old analog network of speakers connected to a common BUS. The audio signal is sent to the shared BUS from the principals office via an amplifier. Each of the speakers has a step-down transformer (100V 1.5--3--6W) which brings the voltage down to a safe level for the 4 Ohm 8W speaker. Specifications on the speaker assembly indicate, that the system uses 100 Volts, though that probably is just the peak voltage when the amp output is very strong. The system is otherwise free of any persistent voltage.
The goal was to somehow inject our own amplified signal trough one of the paralel speaker branches, which should -- in theory -- propagate trough the entire network. If a strong enough amplifier is used, its output can be connected to the transformer (to the speaker side) and it then gets transformed up and travels trough the BUS as if it were sent by the main amp.
Injection prototype
We used old speakers with a small integrated amplifier, which was redirected from the embedded speakers directly to a CINCH (RCA) connector. The opposite side of the connector served as an injection vector.
I connected my phone and started playing a low-volume ~17000 Hz tone using a Signal Generator, which -- we hoped -- none of the staff would hear, but we would. As it turned out, our theory was right and the sound could be heard coming from all of the speakers around the entire school.
Since we were at it, our plans included a persistent backdoor, which we could use to play any sounds remotely. The idea was to use a RaspberryPi with a USB sound card connected to our amplifier. The RPi would be accessible via SSH and any audio could be played wither from local storage, or streamed. This injection could also be planted to any client on the BUS.
Conclusion
We obviously did not finish the persistent backdoor, nor did we ever play anything else besides few more low-profile tests. It was fun to analyse the system and test our theories and we certainly did learn a lot, but further poking would only cause trouble. I feel as though my students found a new passion in hacking and systems security, not only in the virtual world.